
In this post we’ll see how we can add a bit more security to password managers by using a second authentication factor. Multi-factor authentication in general and Two Factor Authentication (2FA) in particular are very broad subjects covered extensively elsewhere.
First factor is represented by something the user knows - the password, and the second one by something he has - a device for generating tokens. The main idea is that OTPs are tokens valid only for one login session. They are generated by a device in the user’s possession, and even if captured by an attacker they would be useless.
For the purpose of this post we’ll use KeePass password manager and one-time passwords generated by Google Authenticator as the second factor. They both support HMAC-based OTPs. So let’s dive in and see how to configure everything.
This post is part of the Security Bricks tutorials - simple methods and habits to build a deliberately secure operational environment, for personal and business use. The other parts below:
- Part 1 - Physical OPSEC basics
- Part 2 - Preventing evil maid attacks
- Part 4 - Using tokens in Ubuntu with PGP
- Part 5 - Token-based authentication for SSH
- Part 6 - Use a Bluetooth device for better security
HOWTO
1. Install Keepass
- KeePass is available for a variety of platforms. So install it either from the repos of your distribution if already present, or download it from the official website. I’ll focus on Ubuntu 16.04 here, which has KeePass 2.32 already in the repositories.
$ sudo apt-get install keepass2
2. Install OtpKeyProv plugin
- Download the OtpKeyProv plugin.
- Unzip the extension and copy the .plgx file to KeePass2 folder:
$ sudo cp OtpKeyProv.plgx /usr/lib/keepass2/
- Notice that keepass2 command is just a wrapper to launch KeePass.exe using Mono:
$ file `which keepass2`
/usr/bin/keepass2: POSIX shell script, ASCII text executable
$ cat `which keepass2`
#!/bin/sh
exec /usr/bin/cli /usr/lib/keepass2/KeePass.exe "$@"
- PLGX plugins are compiled and stored in a plugin cache directory on the user’s system. For Linux, the Mono C# 4.0 compiler is needed, in order to compile the plugin. This is done when starting KeePass. More precisely, for Ubuntu we need the mono-dmcs package:
$ sudo apt-get install mono-complete
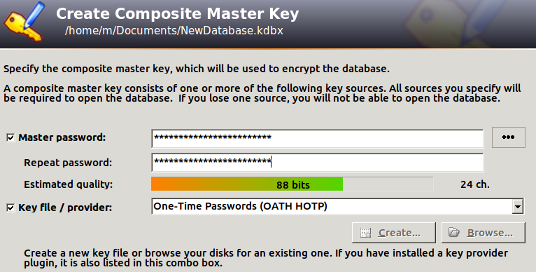
3. Create a new database
- Create a new database (File→New)
- Setup a complex master password
- Select Key file/provider: One-Time Passwords (OATH HOTP)
- Click OK
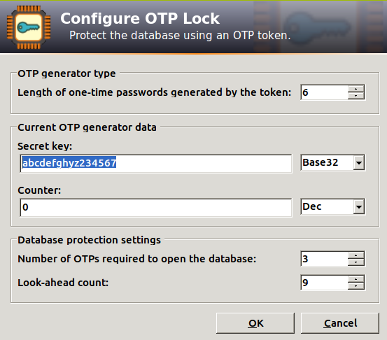
4. Configure the OTP parameters
- Length of one-time passwords: 6
- Secret key: In order to be compatible with Google Authenticator, the secret key must be in Base32. The charset is: [a-z] + [2-7]. Its length must be multiple of 8 characters. Let’s use for example abcdefghyz234567.
- Counter: 0 (Dec)
- Number of OTPs required: 3
- Look-ahead count: 9. This allows for 3 failed KeePass unlock attempts using generated OTPs. After that, the counters will become out of sync, and and the only solution is to recover the database using the secret key:
5. Set up Google Authenticator
- Download and install Google Authenticator
- Enter the app and add a new authenticator
- Select “Enter a provided key” and enter the previous key (e.g. abcdefghyz234567)
- Select “counter based” instead of “time based”

Proceed with caution
- Mind the synchronisation gap - In order to successfully open a databse we need both the database file and the corresponding .otp.xml file. The XML file contains synchronisation related information. So if you backup you .kdbx database file, don’t forget about the XML file!
- Single point of failure -
Password managers are usually regarded as single points of failure. Apply common sense when using them:
- Set an auto-lock timeout after a short period of inactivity
- Use the Two-Channel Auto-Type Obfuscation feature instead of copy-pasting passwords
- Keep the secret key .. you’ve guessed, secret - Because the secret key we set up in step 4 is used to seed the generation of one-time passwords, obviously it needs to be kept secret. Anyone having access to it can bypass the 2nd authentication factor.
- Watch out for resident malware -
Various attacks exist against password managers. For KeePass specifically, we have
KeeFarce which allows the extraction of password databases from memory,
after the database file has been unlocked on the infected user’s machine.
- It is just a matter of time until this tool will end up as a post-exploitation plugin for Metasploit.
- Currently it works on Windows 7 and 8.1 systems. Again, don’t asume it won’t work on Linux.